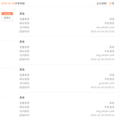
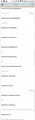
ISP can still know the URLs when DoH running
Version: Firefox 68.1.1, Android 6.0
I did these settings below to turn on the DoH: network.trr.bootstrapAddress:104.16.249.249 network.trr.mode:3 (Others were kept default)
Then, I visited some websites. After a while, I went to the website of my ISP (China unicom) to lookup the details of my data usage, the URLs and visit time were presented there! And were exactly correct ! How??
All Replies (7)
Can you give an example of what exactly is logged by your ISP?
christ1 said
Can you give an example of what exactly is logged by your ISP?
Here are two screenshots: one is the settings config, and the other one is the data usage details I just queried from my ISP's website.
Before that, I had visited the Alibaba's online shopping website -- www.taobao.com. Although the URL of www.taobao.com wasn't presented, some related URLs(aeu.alicdn.com, img.alicdn.com, g.alicdn.com) were still known by my ISP. Are these URLs not resolved via DoH ?
Hi
You may want to try setting network.trr.bootstrapAddress to 1.1.1.1
I have used that setting and it appears to work when I have tried it.
Ti ṣàtúnṣe
See https://cdt.org/blog/dns-strengthening-the-weakest-link-in-internet-privacy/
DoH does improve both, the privacy and security for DNS. However, it does not make you anonymous for your ISP.
When connecting to a website, your ISP still has to carry all your traffic, and has visibility of source and destination IPs. So I suppose your ISP does this deep, granular analysis of your network traffic, and you can see the result on their website. Note, with TLS encrypted traffic they won't see the content of the communication. For unencrypted traffic this gives the ISP (and anyone else looking at web traffic, like the government or hackers) an opportunity to observe your internet usage in great detail, regardless of whether DoH is used for DNS or not.
If the target is to be anonymous for your ISP use a VPN.
Seburo said
Hi You may want to try setting network.trr.bootstrapAddress to 1.1.1.1 I have used that setting and it appears to work when I have tried it.
I've tried 1.1.1.1 address, but it still can't prevent my ISP from observing what URLs I visited.
christ1 said
See https://cdt.org/blog/dns-strengthening-the-weakest-link-in-internet-privacy/ DoH does improve both, the privacy and security for DNS. However, it does not make you anonymous for your ISP. When connecting to a website, your ISP still has to carry all your traffic, and has visibility of source and destination IPs. So I suppose your ISP does this deep, granular analysis of your network traffic, and you can see the result on their website. Note, with TLS encrypted traffic they won't see the content of the communication. For unencrypted traffic this gives the ISP (and anyone else looking at web traffic, like the government or hackers) an opportunity to observe your internet usage in great detail, regardless of whether DoH is used for DNS or not. If the target is to be anonymous for your ISP use a VPN.
Hi, thanks for your warm-hearted help. You said "with TLS encrypted traffic they won't see the content of the communication." But, are the URLs not the content of the communication with TLS encrypted by DoH ?
There were no URLs in your screenshot, just FQDNs of the websites you access. That information can be obtained from the destination IP of the packet(s) generated by your web browser. Those packets have to pass through your ISP, and the IP header isn't encrypted. The actual URL you access on the site is invisible to your ISP, as long as it's a secure site, i.e. if it offers TLS encryption.