Firefox throws SEC_ERROR_BAD_SIGNATURE error for a site but Chromium says certificate is valid
Hi all, I have an Apache site on Kubuntu 20.04 with a certificate signed by my private CA. I've added the root CA ceritificate in Firefox and in Chromium.
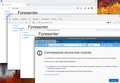
Firefox throws a SEC_ERROR_BAD_SIGNATURE error
Chromium accept the certificate as valid
What can I do?
Notes: the site url is "https://hdev.h.net" (with an internal IP address inside my lab)
Attached there are:
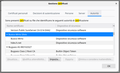
- the authority settings page - the certification authority certificate as seen by Firefox - the site certificate
Firefox version 82.0 Ubuntu Chromium version 86.0.4240.11
தீர்வு தேர்ந்தெடுக்கப்பட்டது
See also:
- Bug 1611381 - Cannot bypass SEC_ERROR_INADEQUATE_KEY_USAGE or SEC_ERROR_BAD_SIGNATURE
- https://tls-observatory.services.mozilla.com/static/certsplainer.html?id=
Try to rename cert9.db (cert9OLD.db) in the Firefox profile folder with Firefox closed.
You can use the button on the "Help -> Troubleshooting Information" (about:support) page to go to the current Firefox profile folder or use the about:profiles page.
- Help -> Troubleshooting Information -> Profile Folder/Directory:
Windows: Open Folder; Linux: Open Directory; Mac: Show in Finder - https://support.mozilla.org/en-US/kb/profiles-where-firefox-stores-user-data
All Replies (13)
There is security software like Avast, Kaspersky, BitDefender and ESET that intercept secure connection certificates and send their own.
https://support.mozilla.org/en-US/kb/firefox-cant-load-websites-other-browsers-can
https://support.mozilla.org/en-US/kb/firefox-and-other-browsers-cant-load-websites
https://support.mozilla.org/en-US/kb/secure-connection-failed-error-message
https://support.mozilla.org/en-US/kb/connection-untrusted-error-message
Websites don't load - troubleshoot and fix error messages
http://kb.mozillazine.org/Error_loading_websites
Well none of the suggested solution worked or is applicable
For now I have: - Firefox version 82.0 Ubuntu error SEC_ERROR_BAD_SIGNATURE - Chromium version 86.0.4240.11 says certificate is valid - Konqueror 5.0.97 says certificate is valid - Epiphany 3.36.4 says certificate is valid
Why Firefox behaves differently?
I don't know why different browsers have a different opinion.
Before we make ourselves crazy over a transient issue, have you cleared Firefox's cache? See: How to clear the Firefox cache.
In theory, this error means "A signature on a certificate is improperly formatted or the certificate has been tampered with."
In your site certificate, it looks like these have the same value:
- ID chiave soggetto
- ID chiave autorità
And also:
Autorità di certificazione => Si (Certificate Authority => Yes)
Is it meant to be a self-signed certificate??
Well, I cleared the cache and the problem persist.
To create certificate I used these step:
- create a private key for CA: sudo openssl genrsa -out hrootCA.key 2048 - create a CA certificate: sudo openssl req -x509 -new -nodes -key hrootCA.key -sha256 -days 3650 -out hrootCA.pem - create a server key and csr request (openssl configuration below) : sudo openssl req -new -sha256 -nodes -newkey rsa:2048 -keyout hdev.key -out hdev.csr -config openssl.cnf - create the server certificate signed by the CA: sudo openssl x509 -req -in hdev.csr -CA hrootCA.pem -CAkey hrootCA.key -CAcreateserial -out hdev.crt -sha256 -days 3650 -extfile openssl.cnf -extensions v3_ca - installed the hdev.cert and hdev.key in Apache - installed hrootCA.pem in Firefox
openssl.cnf contains:
=====================================
[req] default_bits = 2048 distinguished_name = req_distinguished_name prompt = no
[req_distinguished_name] C = IT ST = Italy L = Rome O = Localhost CA OU = Laboratory CN = hdev
[v3_ca] subjectAltName = @alt_names
[alt_names] DNS.1 = hdev DNS.2 = *.h.net
=====================================
What I'm doing wrong?
Well, I cleared the cache and the problem persist.
To create certificate I used these step:
- create a private key for CA: sudo openssl genrsa -out hrootCA.key 2048 - create a CA certificate: sudo openssl req -x509 -new -nodes -key hrootCA.key -sha256 -days 3650 -out hrootCA.pem - create a server key and csr request (openssl configuration below) : sudo openssl req -new -sha256 -nodes -newkey rsa:2048 -keyout hdev.key -out hdev.csr -config openssl.cnf - create the server certificate signed by the CA: sudo openssl x509 -req -in hdev.csr -CA hrootCA.pem -CAkey hrootCA.key -CAcreateserial -out hdev.crt -sha256 -days 3650 -extfile openssl.cnf -extensions v3_ca - installed the hdev.cert and hdev.key in Apache - installed hrootCA.pem in Firefox
openssl.cnf contains:
=====================================
[req] default_bits = 2048 distinguished_name = req_distinguished_name prompt = no
[req_distinguished_name] C = IT ST = Italy L = Rome O = Localhost CA OU = Laboratory CN = hdev
[v3_ca] subjectAltName = @alt_names
[alt_names] DNS.1 = hdev DNS.2 = *.h.net
=====================================
What I'm doing wrong?
Well, I cleared the cache and the problem persist.
To create certificate I used these step:
- create a private key for CA: sudo openssl genrsa -out hrootCA.key 2048 - create a CA certificate: sudo openssl req -x509 -new -nodes -key hrootCA.key -sha256 -days 3650 -out hrootCA.pem - create a server key and csr request (openssl configuration below) : sudo openssl req -new -sha256 -nodes -newkey rsa:2048 -keyout hdev.key -out hdev.csr -config openssl.cnf - create the server certificate signed by the CA: sudo openssl x509 -req -in hdev.csr -CA hrootCA.pem -CAkey hrootCA.key -CAcreateserial -out hdev.crt -sha256 -days 3650 -extfile openssl.cnf -extensions v3_ca - installed the hdev.cert and hdev.key in Apache - installed hrootCA.pem in Firefox
openssl.cnf contains:
=====================================
[req] default_bits = 2048 distinguished_name = req_distinguished_name prompt = no
[req_distinguished_name] C = IT ST = Italy L = Rome O = Localhost CA OU = Laboratory CN = hdev
[v3_ca] subjectAltName = @alt_names
[alt_names] DNS.1 = hdev DNS.2 = *.h.net
=====================================
What I'm doing wrong?
Sorry. Reposted because I didn't see the answer applear.
Please delete duplicated posts.
Thanks
Sorry, this is not the best site for guidance on OpenSSL.
Sorry, I was not clear.
I don't asked for openssl guidance.
I asked: why the command I used generate a certificate /certification authority that every browser accept excluded firefox?
Firefox needs some particular configuration, protocol or algoritm to accept a certificate?
Sorry, what I meant was, perhaps on a forum related to OpenSSL you can find a discussion of issues related to certificate signature problems in Firefox.
Other than what I observed before about the certificate key and signature key being the same -- which is strange if you are signing with a different certificate -- I don't know why Firefox would object to the certificate signature.
Perhaps another forum volunteer knows of a way to find more detailed error information.
தீர்வு தேர்ந்தெடுக்கப்பட்டது
See also:
- Bug 1611381 - Cannot bypass SEC_ERROR_INADEQUATE_KEY_USAGE or SEC_ERROR_BAD_SIGNATURE
- https://tls-observatory.services.mozilla.com/static/certsplainer.html?id=
Try to rename cert9.db (cert9OLD.db) in the Firefox profile folder with Firefox closed.
You can use the button on the "Help -> Troubleshooting Information" (about:support) page to go to the current Firefox profile folder or use the about:profiles page.
- Help -> Troubleshooting Information -> Profile Folder/Directory:
Windows: Open Folder; Linux: Open Directory; Mac: Show in Finder - https://support.mozilla.org/en-US/kb/profiles-where-firefox-stores-user-data
It worked. For the history, the step I followed.
- stop Firefox
- delete cert9.db
- start firefox
- before everything else import hrootCA.pem in the Autorities certificates
- access the certificate protected page
Firefox still complain that there is something wrong with the certificate (it says that a security exception was added to this site); but correctly access the page without asking anything
Thanks a lot
I had the same issue.
Removing cert9.db didn't help, since it simply removed the private CA cert that I added.
What helped was importing the CA cert in the DER format, instead of Base64/PEM/CRT-encoded.