SSL on v.36.0.1 Padlock and Identity Info Missing
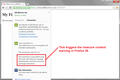
When I visit an https:// url on Firefox version 36.0.1 I am getting an exclamation mark instead of a padlock::
SCREENSHOTS:: http://www.silkblooms.co.uk/images/prototypes/ssl3.jpg http://www.silkblooms.co.uk/images/prototypes/ssl2.jpg http://www.silkblooms.co.uk/images/prototypes/ssl1.jpg
The same websites are showing identity information and padlocks when I use other browsers like Chrome or IE so the problem is with FF. I have no proxy in the tools>options>advanced>network>settings (so it's not that).
Zgjidhje e zgjedhur
Our host has fixed this::
They have adjusted the SSLCipherSuites to resolve this as can be verified at:
https://www.ssllabs.com/ssltest/analyze.html?d=silkblooms.co.uk&hideResults=on
Finally!
Thank you everyone for helping me here.
Lexojeni këtë përgjigje brenda kontekstit 👍 0Krejt Përgjigjet (19)
hi MJ_Lind, the site you have mentioned only offers weak TLS_RSA_WITH_RC4_128_SHA encryption making use of the RC4 cipher suite which is considered broken and no longer trustworthy. according to this recent proposal browsers have to stop supporting RC4: https://tools.ietf.org/html/rfc7465
starting with firefox 38, the browser will show an error message and totally block access to affected sites, so please raise this issue with your hoster...
philipp said
hi MJ_Lind, the site you have mentioned only offers weak TLS_RSA_WITH_RC4_128_SHA encryption making use of the RC4 cipher suite which is considered broken and no longer trustworthy. according to this recent proposal browsers have to stop supporting RC4: https://tools.ietf.org/html/rfc7465 starting with firefox 38, the browser will show an error message and totally block access to affected sites, so please raise this issue with your hoster...
Hi Philipp,
Is this on www.silkblooms.co.uk? Where are you getting that info from so I can raise this with the certificate issuing company?
David....
hi david, you can check this with a tool like https://www.ssllabs.com/ssltest/index.html
and this is the bug that will remove support for rc4 cipher-suites in firefox 38: https://bugzilla.mozilla.org/show_bug.cgi?id=1124039
Hi Phillip,
Thank you for this info. I will be able to upgrade the certificate as it would appear this is the problem.
David...
it will be less about the certificate (yours looks ok), but about the configuration of the web-server where your site is running, so please raise the issue with the hosting provider...
I see.... ok I don't really see as I don't know exactly how to advise our hosting provider. Do you know the specific, technical jargon that I should present to the host? If you were contacting your hosting provider about this then exactly what would you say to them?
you can tell them that you have learned that the server where your website is hosted only offers a weak RC4 cipher suite for encryption, which most browsers will stop supporting soon & that means that your visitors will only see an error message - as a reference you can give this site: https://developer.mozilla.org/en-US/Firefox/Releases/38/Site_Compatibility#Security
the workaround is to update the server's configuration to make use of more state-of-the art encryption...
The host is blaming the certificate::
"I believe the issue should be fixed if we reinstall SSL for the domain, is there any chance that you could get in touch with the SSL provider and get a new cert to comply with the new SHA-2 requirement?"
Is this accurate what they're saying?
you'll ultimately have to figure it out together with the support of your hoster... i can only repeat myself though: the error that firefox is showing is due to the server only using a weak TLS_RSA_WITH_RC4_128_SHA cipher suite, which is not related to your certificate but to the server's configuration that should be under the control of the hoster.
Your certificate was signed with "SHA256". I think the issue the host is describing with the "SHA1" certificate refers to the bundle of additional certificates your cert issuer gave you along with your own site certificate. Your web server sends the bundle with your certificate as part of the chain showing that a trusted root certificate was used to sign your certificate. (Without this chain, Firefox will display the unknown issuer error page.) Maybe they have an upgrade to the bundle that you can install in place of the one you have?
But I don't think that's the current issue. To prevent your server from using an RC4 Cipher, I believe you need to edit your HTTP configuration file (httpd.conf), which may or may not require intervention from your host. The SSLCipherSuite directive is the setting that restricts cipher suites on Apache.
Mozilla has an article on cipher suites and how restrictions affect different browsers and operating systems: https://wiki.mozilla.org/Security/Server_Side_TLS.
I'm getting nowhere with this. Over a day later an several emails between myself, Trustico and out host. No one knows what's causing it. Here's what's happened so far::
- Trustico have verified that the certificate is installed correctly and they're adamant that the fault lies with insecure items in the source code. They can't list any such item.
- Our host has re-installed the SSL. It is EV SSL CA - G4 so it's a good, up-to-date certificate.
- Trustico and our host are both blaming it on the website having insecure items. None of them can exmplain this empty webpage though. Look at the source code as it knock their arguement on the head:: https://www.silkblooms.co.uk/ssl/ff.html
I'm at a complete loss. This was the last email from Trustico Support::
Dear David,
Thank you for your reply
I am afraid that is what Firefox is telling you about the certificate and why it is not being displayed.
I can't give you anymore information. I have helped you are far as I can now.
I have checked the certificate installation it is working fine. The keys are correct, I have visited our other clients using the same certificate and keys and they have no problems.
I have even checked with our clients that are still using the out of date SHA-1 software and they all still have the green bar.
I have even given you one to compare I am also using 36.0.1 version of Firefox
https://ssltools.websecurity.symantec.com/checker/views/certCheck.jsp You can type in your domain name and see the installation
Then you can type in - www.studiocoast.com.au who I helped with a similar issue but it was with Chrome. https://www.studiocoast.com.au/ - now visit Firefox on his web site.
The green bar and his organisation name comes up with no problems. Now referring back to the SSL certificate, except for the domain name you will noticed every single other data is the same in regards to signature strength and root chain that is being used. He is using GeoTrust EV SSL CA - G4 and so are you.
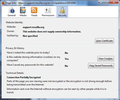
The only difference is that Firefox is telling you, "The connection to this website is not fully secure because it contains unencrypted elements (such as images)." and that is why it is not showing the Green Bar and padlock.
There must be something on your site, that is linking to something that is no secure, I am not 100% sure it is the only possibility after doing all the comparison for all our other EV certificate clients, both SHA-1 and SHA-2 using the exact same Roots CA's as you, or even the old one you had installed.
Kind regards,
Robert Craker Trustico® Online Limited www.trustico.com
Yes, this is very frustrating. Did they look at the screenshot from Chrome showing its analysis of the certificate? (New capture attached.) I shouldn't say it's an analysis of the certificate. The certificate is great. It's a comment on the SSL ciphers offered by the server to the browser.
The comparison server they gave you actually is Windows-based and uses Microsoft's IIS webserver software and not the Apache webserver, so it's not apples-to-apples. Or in other words, it doesn't prove they know how to configure Apache.
Ndryshuar
Thank you. I've sent this to the host. Are you saying that the problem is definitely, 100% with the Apache server configuration and not with the certificate?
I see this same issue on this very URL
wizzardz said
I see this same issue on this very URL
You should start a new thread as this thread is a still active on a similar yet different thing.
Zgjidhja e Zgjedhur
Our host has fixed this::
They have adjusted the SSLCipherSuites to resolve this as can be verified at:
https://www.ssllabs.com/ssltest/analyze.html?d=silkblooms.co.uk&hideResults=on
Finally!
Thank you everyone for helping me here.
Ndryshuar
Not sure how is different, but I will start a new thread if that's what's needed
You can also look at this extension:
Ndryshuar
Marking solution as suggested in /flagged