How to determine which software is performing HTTPS scanning?
In my work computer, Firefox always gives "sec_error_unknown_issuer" error and only on HTTPS sites.
I have browsed the forums and understood that this is most probably caused by a sofware that performs HTTPS scanning. (See [this](https://support.mozilla.org/en-US/questions/1030927) and [this](https://support.mozilla.org/en-US/questions/1026631#answer-650916) answer)
However, I really don't know which software is performing the HTTPS scanning exactly.
Is there a way that I can determine which software is doing the HTTPS scanning so that I will be able to add its certificate to Firefox and hence be able to use the Firefox properly?
Thank you very much in advance
Regards
გადაწყვეტა შერჩეულია
Apparently the proxy which uses the KFSCaRoot certificate (which doesn't yield much in a search) is imperfect if it allows some sites to bypass it.
Try using Chrome for this next step, which is to view and export the signing certificate, assuming you trust whatever that is to read all your traffic.
Export
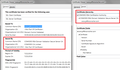
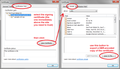
- Open a secure site in Chrome and click the padlock icon on the address bar. Click Connection to find the link to View Certificate.
- In the Chrome certificate viewer, switch to the the Certification Path tab. Click the cert you want to export and use the View Certificate button to open it directly. (This is not the site's certificate, but the certificate used by the proxy to sign the fake site certificates.)
- Then click the Details tab and click the Copy to file button. This starts the Export Wizard. Use the DER format and save to a convenient location.
Import
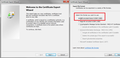
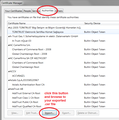
- In Firefox, open the Certificate Manager using: "3-bar" menu button (or Tools menu) > Options > Advanced > Certificates mini-tab > "View Certificates" button
- Click the Authorities mini-tab and then the "Import" button, and find the DER file. Note: I suggest allowing the certificate for websites only unless your IT suggests otherwise.
I am attaching some screen shots for reference, obviously not with your actual proxy...
Does it work?
პასუხის ნახვა სრულად 👍 5ყველა პასუხი (8)
Some Antivirus clients have been known to do this on Windows.
I know but is there a way to determine it precisely within the Firefox maybe?
What security software do you have?
There is security software like Avast and Kaspersky and BitDefender that intercept secure connections and send their own certificate.
Open the "Add Security Exception" window by pasting this chrome URL in the Firefox location/address bar and check the certificate:
- chrome://pippki/content/exceptionDialog.xul
In the location field of this window type or paste the URL of the website.
- retrieve the certificate via the "Get certificate" button
- click the "View..." button to inspect the certificate in the Certificate Viewer
You can inspect details like the issuer and the certificate chain in the Details tab of the Certificate Viewer. Check who is the issuer of the certificate. If necessary then you can attach a screenshot that shows the certificate viewer.
If you need a test site, you could try this page:
https://jeffersonscher.com/res/jstest.php
You likely will get an error page. Expand the "I understand the risks" section and look for an Add Exception button.
Note: You don't need to complete the process of adding an exception -- I suggest not adding one until we know this isn't a malware issue -- but you can use the dialog to view the information that makes Firefox suspicious.
Click Add Exception, and the certificate exception dialog should open.
Click the View button. If View is not enabled, try the Get Certificate button first.
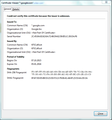
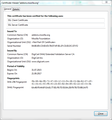
This should pop up the Certificate Viewer. Look at the "Issued by" section, and on the Details tab, the Certificate Hierarchy. What do you see there? I have attached a screen shot for comparison.
Thanks for the answers.
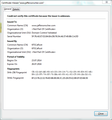
I have looked at the certificates for "google.com" and "www.jeffersonscher.com".
In both websites, the issuer is the same. However, their serial numbers are different.
I am attaching the screenshots.
So how should I add the certificate to Firefox now?
Regards
ჩასწორების თარიღი:
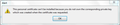
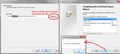
Follow up: I have exported the *google.com certificate and tried to add it to "Your Certificates" part but I got the error in the screenshot.
Also, the problem still continues on every website but interestingly, when I tried to connect to "addons.mozilla.org", it connects but in plain HTML version. I am attaching the screenshot of the certificate.
ჩასწორების თარიღი:
შერჩეული გადაწყვეტა
Apparently the proxy which uses the KFSCaRoot certificate (which doesn't yield much in a search) is imperfect if it allows some sites to bypass it.
Try using Chrome for this next step, which is to view and export the signing certificate, assuming you trust whatever that is to read all your traffic.
Export
- Open a secure site in Chrome and click the padlock icon on the address bar. Click Connection to find the link to View Certificate.
- In the Chrome certificate viewer, switch to the the Certification Path tab. Click the cert you want to export and use the View Certificate button to open it directly. (This is not the site's certificate, but the certificate used by the proxy to sign the fake site certificates.)
- Then click the Details tab and click the Copy to file button. This starts the Export Wizard. Use the DER format and save to a convenient location.
Import
- In Firefox, open the Certificate Manager using: "3-bar" menu button (or Tools menu) > Options > Advanced > Certificates mini-tab > "View Certificates" button
- Click the Authorities mini-tab and then the "Import" button, and find the DER file. Note: I suggest allowing the certificate for websites only unless your IT suggests otherwise.
I am attaching some screen shots for reference, obviously not with your actual proxy...
Does it work?