ESET antivirus security detections on specific Thunderbird Gmail emails
Hello,
Looking for your expertise on this scenario. Would really appreciate any advise.
Thunderbird is syncing on my Windows 11 PC newly and it's working fine. However, I use ESET's security solution with their ESET Internet Security anti-virus product and it has detected some security incidents with some specific Gmail label that have emails within the Thunderbird folders. Also, the usual ESET scan doesn't catch these. I had discussed with ESET technical support and they said that the 'In -Depth' scan feature needs to be used for the scanner to get inside the compressed file to search inside it and then it will check for security detections. Other way would be to extract the compressed file to a folder and then run a usual scan on the extracted items. But, as explained below, the compressed specific Thunderbird file can't seem to be extracted either.
I was trying to extract the specific Thunderbird file which has been detected in the real time system background scan, with 7-Zip as it shows the 'Extract' option. But, it doesn't extract and gives an error that it couldn't extract the specific Thunderbird file.
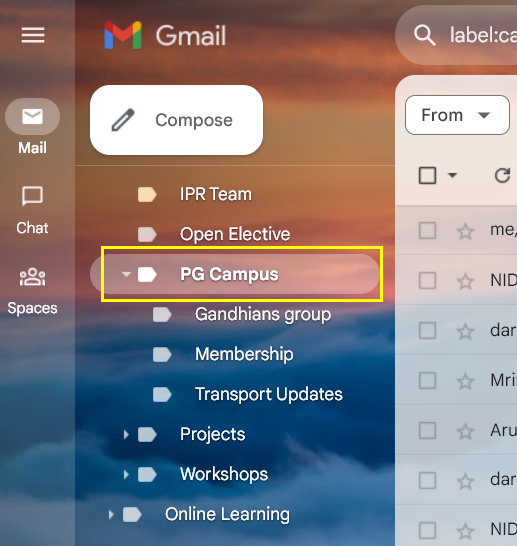
The specific file name is a label in my Gmail mailbox which has some emails, which Thunderbird has downloaded to it's cache.
Q: So, could anyone please let me know how do I extract or view which specific email item within the single specific Thunderbird file 'PG Campus.file' could the email item be in that may be infected, or whatever security issue has been detected?
3 Screenshot attached for your ref.
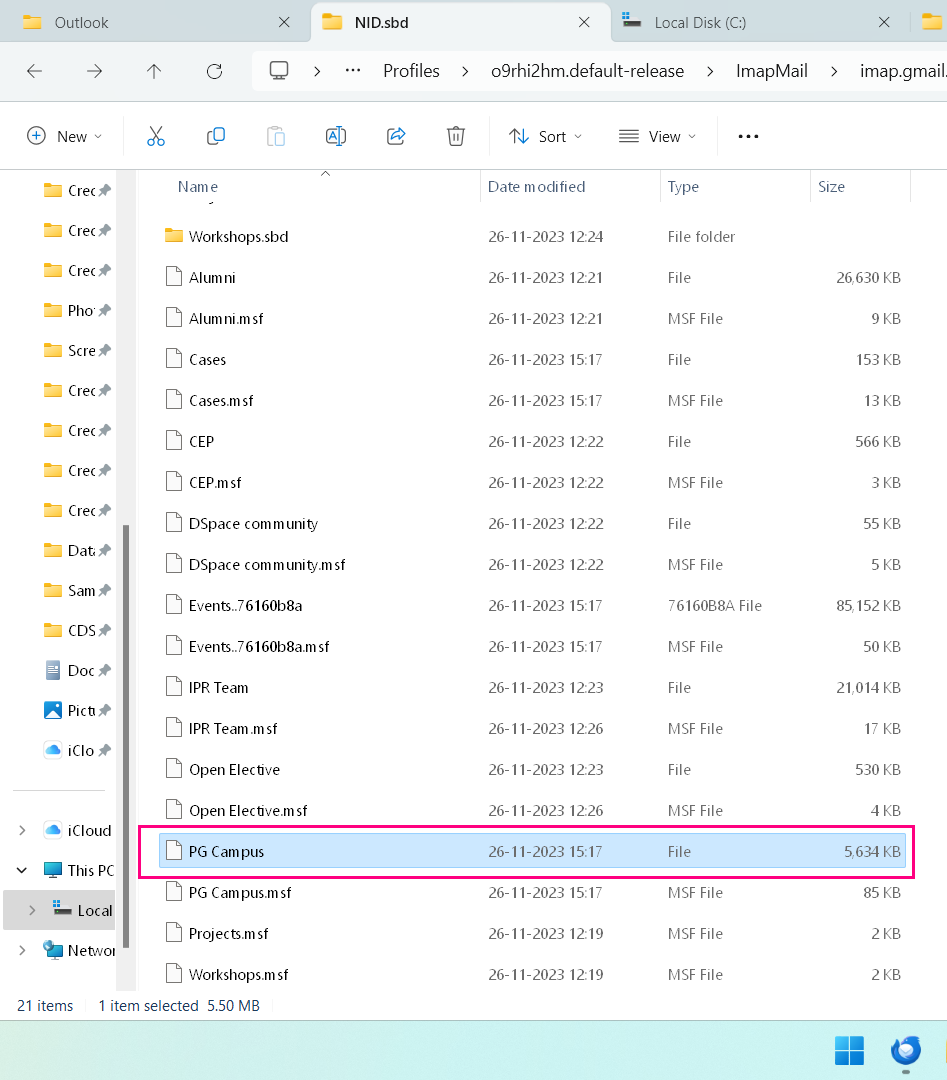
Security detection of one of them is at: C:\Users\User\Application Data\Thunderbird\Profiles\o9rhi2hm.default-release\ImapMail\imap.gmail.com\Career.sbd\NID.sbd\PG Campus
The 'PG Campus' label based filed has no filename extension, but it has a size of 5.5 MB which has 58 emails as I checked on the Gmail web mail.
すべての返信 (2)
Personally I think just flag it and ignore it.
The "threat" is identified as a javascript threat. Thunderbird does not run javascript on email bodies, like having ammunition in your home, it is not dangerous unless it is loaded in something that can make it go bang. Like Microsoft Outlook, which will execute the javascript. In Thunderbird all it does is consume a few bytes of space. Completely inert.
The file you have identified is a plain text file, It is an MBOX file (RD variant) with a small Mozilla twist in the formatting of the From line. MBOX is the default mail storage file format for Thunderbird. There is nothing to extract from it other than text so of course 7-zip is not going to extract anything, nor is Esets deep scan.
You can open the file and read it in windows notepad if you want to see what is in it. What you will see is the raw text that makes up the emails source in the folder one email following he other. essentially a stack of EML files. https://www.loc.gov/preservation/digital/formats/fdd/fdd000385.shtml
I have no idea what rubbish the Eset folk are selling you in their support, I did used the product until a couple of years ago and around 10 years ago it was very good. A couple of years ago I figured the money I was giving them for a load of alarmist warnings about javascript marketing and tracking code on web pages was a poor exchange. So now I use defender.
Generally antivirus scanners actually decode the mime portions of emails so they can examine the HTML body and attachments. Apparently Eset do not do this. Personally I wonder why they do this scanning at all in text files. For years I have been recommending to people that they exclude the Thunderbird profile from all scanning activity other than periodic scans, because A/V usually causes more issues with email than it solves ad this is a perfect example.
Eset have consumed your time, and now mine discussing what is in essence a false positive as it can not actually take any action on your computer unless you save the email as HTML and open it in a web browser. I am sure some people do that, but the A/V product will get two more bites of the apple, once when the HTML file is written/saved, and again when it is loaded in the web browser. They fed you full of rubbish about deep scans for a text file. What they think they can extract from a text file I have no idea at all.
Thank you Matt for taking the time for your explanation and reply!
I'm not referring to the .MBOX file. The two .MBOX files is from Google Takeout's data export feature. However, that is also a similar case, where I'm not being able to view the contents of the 14 GB .MBOX file, as well.
I checked the file in Notepad as you suggested, and see only text. The original emails have some attachments which don't reflect in the Notepad file.
Is it the attachments which ESET is catching these security detections? I mean, why would it detect the security detections only in some of the emails and not all? That means, there's something in some of the detected emails, right?
I wish there was some way for me to view the contents of the specific Thunderbird file which I have highlighted in pink in the screenshot.
Q: Would you know a way, to open the 'PG Campus' folder in Thunderbird's app interface and scan the full folder of 58 emails, via the ESET plug-in, so that I can see if it pin-points which particular email(s) may have security detections?
この投稿は intellogo により