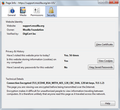
Why am i (or Firefox) not able to use some (stronger) cipher suites on certain sites? ... yes, they are supporting them, checked on ssllabs-test
Can anyone enlighten me on this? I do not want to complain about anything i just try to understand what and why is this happening. (I have nothing better to do today,sorry.)
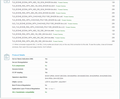
Under the "green lock" -pictures- the ciphers (i think) are TLS1.0 (ex.:ECDHE-RSA-AES128-SHA) based on these software's lists: - OpenSSL - GnuTLS - LibreSSL
So i tried to disable these ciphers (AES128&256CBC-SHA1) on the "about:config" page and leave AESGCM&CHACHA20 ciphers. Then comes the warning: "SSL_ERROR_NO_CYPHER_OVERLAP" , on sites which normally support AESGCM suites.
There are some "missing" (mostly AESCBC-SHA256/SHA384) options from the config page (just for me?), does Firefox support them?:
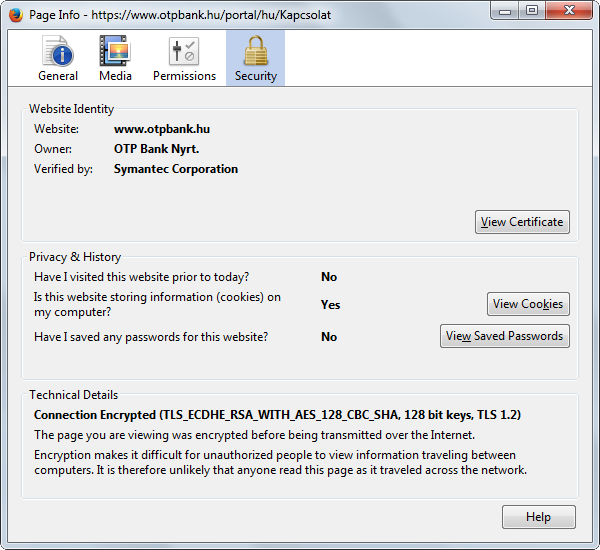
- ECDHE-RSA-AES128(CBC)-SHA256 -The banking site supports this, tested on https://observatory.mozilla.org & https://www.ssllabs.com (but not available by me, must use CBC-SHA1 instead) - ECDHE-RSA-AES256(CBC)-SHA256 - ECDHE-RSA-AES256(CBC)-SHA384 - ECDHE-RSA-CAMELLIA128(GCM&CBC)-SHA256 - ECDHE-RSA-CAMELLIA256(GCM&CBC)-SHA384
- DHE-RSA-AES128(GCM)-SHA256 - DHE-RSA-AES256(CBC)-SHA256 - DHE-RSA-AES256(CBC)-SHA384 - DHE-RSA-CAMELLIA128&256(GCM&CBC)-SHA256 - DHE-RSA-CAMELLIA256(GCM)-SHA384
- ECDHE-ECDSA-AES128(CBC)-SHA256 - ECDHE-ECDSA-AES256(CBC)-SHA384 - ECDHE-ECDSA-CAMELLIA128(GCM&CBC)-SHA256 - ECDHE-ECDSA-CAMELLIA256(GCM&CBC)-SHA384
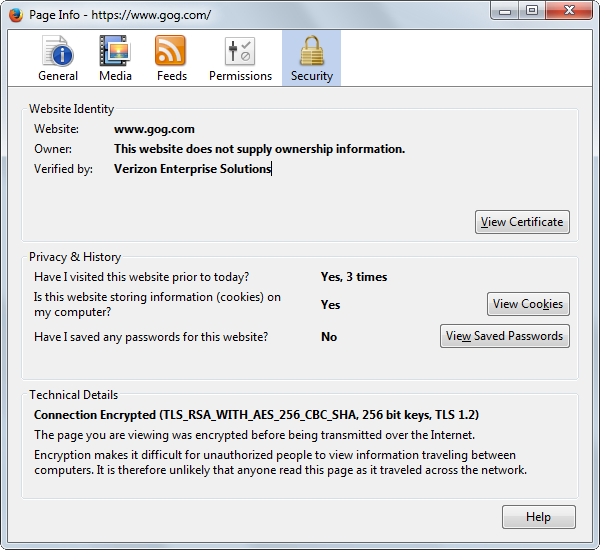
Also https://www.gog.com supports:
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 and TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- https://www.ssllabs.com/ssltest/analyze.html?d=gog.com&s=193.59.178.35
-Firefox supports those too but i can't use them. If RSA-AES128-SHA and RSA-AES256-SHA are disabled the page won't load but it should because of AESGCM is supported on both side.
Why does Firefox switch back to CBC-SHA1 ciphers in these sites? Is it a server-side fault or Firefox "needs help" with this? - Are there any addons or settings that could force the cipher-order? - On Mozilla's Support site (here) everything is fine "i can play" between CBC and GCM (-picture-).
Any help,recommendation,explanation or suggestion appreciated.
Všechny odpovědi (3)
Did you do the a test for Firefox?
Upravil uživatel cor-el dne
I checked other browsers that could solve these but i could not find a single "Mozilla/Firefox-based" one, and the conclusions are:
- I realized that i use Firefox because of its addons.
- Firefox does not allow users to set the ciphersuite-order or support some more from them, like Otter Browser and Dooble Browser.
I have also found a "chromium-based" browser called Iridium:
- (+) Supports x25519 curve. - Firefox does not(!!!)
- (+) Most of my favorite addons work also (KeePass,uBlock,etc).
- (~) chromium killed the 'DHE cipher-suites'
- (-) google fights against symantec's certificates -> always a warning if a site is using a cert signed by symantec
It would be nice to be able to set the client-side ciphersuite-order in Firefox regardless what the 'server-side-tls' topc tells about it.
Here are some pictures ,what other developers did and what should Firefox do:
Upravil uživatel sanyy dne
In Firefox you can disable cipher suites via security.ssl3 prefs on the about:config page. Current Firefox releases only support a very limited set of cipher suites and support for a lot of cipher suites has been removed because they are either too weak or shouldn't be used anymore. You can't change the order in which they are send to a server.