Firefox 28.0 is indicating that my installed Java SE 7 U51 is vulnerable (2014 03 20)
When invoking Firefox "Tools -> Add-ons -> Plugins" and clicking on "Check to see if your plugins are up to date", the checker asserts that Java(TM) Platform SE 7 U51 is vulnerable and I should update now.
The Java version I have installed shows as being the most current version. Re-installing Java does not effect the Firefox-generated warning. Running the web based Java version checker indicates that I have the current version installed.
Do I need to re-install Firefox in order to get the warning to go away, or do I have some kind of gremlin in my system?
Gekose oplossing
It looks that Oracle has released Java 8, so this version might be the latest Java release and has replaced the last Java 7U51 release.
Lees dié antwoord in konteks 👍 9All Replies (12)
Just to make sure, you're doing it the right way:
Please check if all your plugins are up-to-date. To do this, go to the Mozilla Plugin Check site.
Once you're there, the site will check if all your plugins have the latest versions. If you see plugins in the list that have a yellow Update button or a red Update now button, please update these immediately.
To do so, please click each red or yellow button. Then you should see a site that allows you to download the latest version. Double-click the downloaded file to start the installation and follow the steps mentioned in the installation procedure.
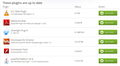
Your System Details List shows the Java 7U51 plugin as installed.
- Next Generation Java Plug-in 10.51.2 for Mozilla browsers
There has been a change in the Java security settings, see:
- "What should I do when I see a security prompt from Java?":
http://www.java.com/en/download/help/appsecuritydialogs.xml
If you visit a website regularly then a possible workaround is to add the URL to the Java Exceptions Site List, see:
- "Why are Java applications blocked by your security settings?":
http://www.java.com/en/download/help/java_blocked.xml - "How can I configure the Exception Site List?":
http://www.java.com/en/download/faq/exception_sitelist.xml
I had already done that . . .
NUMEROUS TIMES
Before I decided that something was catte-wampus ...
It is evident that either I am doing something with my system which is several standard deviations away from the median, or that there is a gremlin in my Norton and Spybot-scanned system, or that there is a bug in how vulnerability is assessed.
I am not getting blocked from accessing web-sites.
I am getting a security flag waved in my face which does not go away when I apply the fix that the flag-waver is suggesting. My perception is that I have a secure version of Java installed, but that the vulnerability checker runs, finds and reports what is believed to be a secure version number, and then reports to me that the (secure) version is vulnerable.
Which leads to the conclusion that either the installed version has been just newly determined to be vulnerable - and no update is available, or that the assessment and reporting web page has a problem ??
If you have the latest Java version and the Java test pages confirm this then you can ignore the Mozilla plugin check page as that page can get it wrong in some cases.
Can you attach a screenshot?
- http://en.wikipedia.org/wiki/Screenshot
- https://support.mozilla.org/kb/how-do-i-create-screenshot-my-problem
Use a compressed image type like PNG or JPG to save the screenshot.
Here is what I am seeing . . .
Gekose oplossing
It looks that Oracle has released Java 8, so this version might be the latest Java release and has replaced the last Java 7U51 release.
The routine update path for Java continues to show SE 7 U51 as the current release.
I followed the link to the Oracle release information and found the download for version 8 and installed it.
The vulnerability checker is now happy.
My risk-aversity can now relax.
Thanks for the clue.
You're welcome.
I hadn't noticed that Java 8 had been released, so I have installed this version as well on Linux.
Cor-el, hi.
I have the same issue with Java 7 u51 being reported on the plug-ins page as 'vulnerable' i.e. out of date despite, as reported earlier, this version being verified by Java as the latest version.
Did you notice that Java 8 is the 'Java Development Package' (JDK) NOT the normal Java SE version provided by the standard download page? JDK includes a lot of functionality not required by anyone but Java developers so I will be waiting for the next Java SE standard update: but it would appear that the Firefox plug-ins page is not in this case distinguishing between Java JDK and Java SE and hence the erronous 'vulnerability' report.
Coe-el, hello again.
Quickly, a minor correction: I distinguished between Java JDK and Java SE - I should have said Java SE JDK and Java SE Runtime Environment (Java RE). Java JDK does include JRE for development purposes of course. Apologies for the error.
Just a brief update for anyone who is still following this thread.
I have been checking frequently since my last post for Java SE Runtime Environment updates (JRE) and JRE 7 u55 has just arrived: having installed it, however, FF insists, as for JRE 7 u51, that it is vulnerable and needs updating. I am not going to download and install Java SE JDK version 8.0 - the development kit - which I don't need, but I do suggest that FF developers better distinguish between JDK and JRE: this distinction, to be fair, has in my experience worked pretty well in the past, but when it doesn't it can be unnecessarily confusing and for some worrying - as this thread has shown.